IoT Revolution: How to Protect Your Data When Everything is Connected?

The Internet-of-Things, or IoT, refers to a system of integrated digital devices connected in a network through which they communicate seamlessly without intervention. IoT devices are all around us; cars, smartphones, surveillance cameras, smart electronics — the list goes on. IoT not only affects data but also transforms the how, when and where of collecting it. IoT technologies are changing the way things are built and is creating new opportunities for businesses.
The idea of IoT is not new. The first IoT device dates back to 1990 in the form of a toaster that could be switched on and off over the internet. Since then, the concept has taken the world by storm and revolutionized the way we operate. This IoT revolution, however, comes with certain risks and challenges.
Challenges in the IoT Ecosystem
The gathering and analysis of data are some of the essential aspects of IoT. It gives rise to potential privacy and security problems, as the gathered data needs to be protected throughout its life cycle. And since this data flows through many devices, networks, and administrative boundaries, its privacy, security, and integrity are challenged at multiple stages.
IoT ecosystems are built up using a fabric of interconnected devices, communication protocols and media, network devices and so on. Regardless of the nature of business processes that employ IoT networks, there is a heavy reliance on device manufacturers, solution providers, cloud providers, systems or service providers, network equipment manufacturers and so on. All these are the unknowns in this equation, adding to the complexity of managing data flow, and performing analysis and extracting actionable business insights.
In such a scenario, it is difficult to get data securely to the right place, at the right time, to the right people and in the right format. There’s a lot that can go wrong — many places a breach can occur.
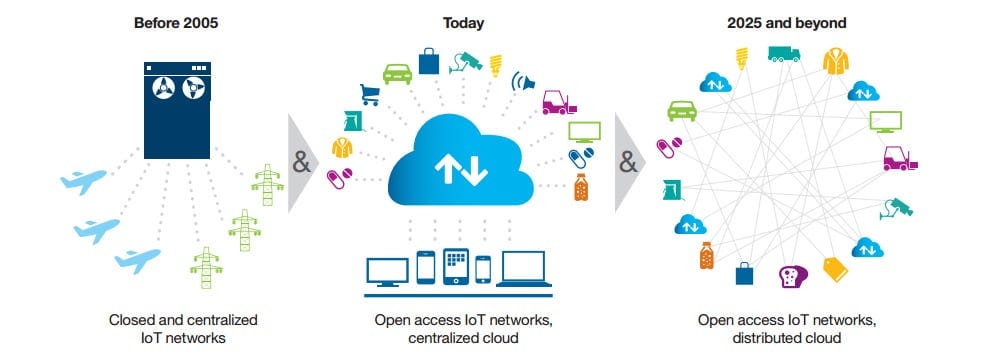
IoT Networks are Centralized
Current IoT ecosystems rely heavily on centralized communication models. All devices are identified, authenticated and connected through centralized cloud servers that have high computing capacities. A connection between devices often has to go through the internet, even if they happen to be a few feet apart.
This model has worked well in the past and will continue to work for small-scale applications. However, such a model can hardly be expected to keep supporting the growing needs of the vast IoT ecosystems in the future.
Blockchain as a Potential Solution
The answer potentially lies in a decentralized approach to IoT networking. A P2P (peer-to-peer) communication protocol for processing billions of transactions between devices can significantly reduce the costs associated with maintaining large data centers. It will also avoid single points of failure, making the ecosystem more robust and scalable. However, P2P networks have challenges of their own, namely the protection of data privacy and security. The integrity of data needs to be maintained, and there needs to be a consensus between various IoT nodes on how to create and share data without external influences such as data spoofing.
Blockchain networks address a majority of these concerns. These are decentralized, peer-to-peer networks that are resistant to data manipulation and corruption. It is achieved through an established consensus protocol for the creation and sharing of data. Each data transaction is verified by every participant in the network, and faulty or malicious input is discarded right away. It ensures data integrity across the board which is scalable to large networks performing billions of transactions.
The blockchain technology also solves the problem of data privacy and security. Public blockchains such as the Bitcoin blockchain are accessible to anyone. However, private blockchains can be established for driving IoT networks. These are permissioned blockchains, and only allow participation through invitation. The participation of a new node can either be allowed by consensus of all existing nodes, or by the start of the blockchain or policies set up by this starter. This will make it incredibly difficult for a malicious user to gain access to the network.
Permissioned blockchains also offer a high level of data privacy. Only nodes involved in a transaction can access it and verify it. Other nodes will not be able to access this data, thus ensuring privacy at a much granular level.
Final Thoughts
The blockchain technology is all set to revolutionize the face of many industries and technology sectors. Supply chains, food, and healthcare, even industrial applications can benefit from this technology. The reason it isn’t mainstream yet has to do with the fact that this technology is still in its infancy, and will require at least a few years for the development of standardized practices in the area.
®“LuxTag”, Trademark registered.



