Can Novel Technology Security Protocols Allow Secure Remote Manufacturing?
The decade of 2020–2030 will see new approaches to manufacturing and logistics of industrial parts. Along with them, enhanced counterfeiting potential will emerge, and that deserves appropriate security measures to curb them right from the start.
In 2017, a New York patient received a locally 3D printed sternum and rib cage implant, which was produced by the Commonwealth Scientific and Industrial Research Organisation (“CSIRO”) in Australia. Source: ZDNet.
 To remind you what’s the sternum is— see above.
To remind you what’s the sternum is— see above.
Yes, technology has advanced a lot, and printing of 3D objects has by far grown beyond producing little showcase objects. I’m sure you remember the small colorful objects which used to be printed to proudly convince us that printers are no more limited to 2D.
 There are already home-printable face masks available for download from sites like https://grabcad.com/library/cotton-pad-face-mask-1.
There are already home-printable face masks available for download from sites like https://grabcad.com/library/cotton-pad-face-mask-1.
Actually, numerous sites exist to cater for sharing of STL 3D model files amongst the community of enthusiasts. To name some, this would be Grabcad.com, Turbosquid.com, Artec3D.com, Cults3D.com, Free3D.com, Hum3D.com, and many others. Some of these model files are paid and come with certain licenses. For your information, we’re dealing with a standardized file format called “.STL” (STereoLithography, or Standard Tessellation Language) format. STL files are generally compatible with the software handling 3D model files, as well as with the majority of 3D printers.
Back to industrial applications — Manufacturers of machinery parts are starting to consider not only to use 3D Printing locally to drive rapid prototyping but are seriously looking into manufacturing remotely. That means, on-site (on-customers’-site!) manufacturing can become a reality, suchlike the aforementioned case of the medical implant produced near the operation theatre.
Recently, we hear the term “additive manufacturing” more often, which, according to GE, is “yet another technological advancement made possible by the transition from analog to digital processes”. GE goes on “Additive manufacturing uses data computer-aided-design (CAD) software or 3D object scanners to direct hardware to deposit material, layer upon layer, in precise geometric shapes. As its name implies, additive manufacturing adds material to create an object. By contrast, when you create an object by traditional means, it is often necessary to remove material through milling, machining, carving, shaping or other means.”
 CAD model for 3D printing.
CAD model for 3D printing.
Now, when we add digital delivery via online means to the additive manufacturing 3D printing system — we can remove the traditional at-factory QC (Quality Check), wrapping, shipping, and transportation to the installation location from the supply-chain equation. This is fascinating but needs special consideration of the dangers it brings along.
“The convergence of the Internet, digitized music and media players has had dramatic consequences for music copyright. 3D printing technology may have similar implications for artistic copyright, design right, trademarks, and patents, but in a rather more diverse legal framework.” ― Bradshaw, et al., (2010), “The intellectual property implications of low-cost 3D printing,” scriptEd, 7(1), 5–31.
I think you see the problem. When a manufacturer shifts the production outside his controlled premises when they send files to “print” to their customers — how can they ensure that the customer The Atlantic Council, a U.S. based organization aiming to shape solutions to global challenges noted implications of 3D printing for counterfeiting & anticounterfeiting. Their 2011 (not the youngest!) Strategic Foresight Report titled “Could 3D Printing Change the World?” touches on this, and I highly recommend the read.
Let me touch on possible paths of mitigation. This is not an exhaustive list of solutions. It is mere food for thought to instigate solution-finding for the obstacle of counterfeit re-printing and theft of intellectual property when remote 3D print manufacturing. 2. a. Upgrade the printer with special technology and modified driver 2. b. Install a mini-computer at the manufacturing site, which controls the printing system
1.Maintain ownership and control of the remote additive manufacturing When the branded manufacturer company owns the remote printing equipment, operates staff at the location and ideally, controls the premises. In essence, the job to secure the remote production from leakages becomes more simple. Material input and output has to be monitored, the printer’s counter (like a car mileage odometer) can be tapped into. The remote manufacturing location can be connected to the HQ via secure data links, for example, OpenVPN or WireGuard. An optional CCTV system can be used. For the purpose of this document, I will focus on path two more.
2.Non-controlled remote additive manufacturing This path describes the use-case where the printing equipment is not under full control of the brand owner.
We assume the manufacturer to operate a blockchain-powered cloud solution (containing various digital services), which caters for the accounting of unique objects and their lifecycle. Such life cycles shall be designed to start with the “creation” upon order placement or payment. The accounting can comprise allocation of ownership and further features.
Variant A) We use a unique, internet-enabled printer driver software The remote workstation, in the vicinity of the printing system, is equipped with a specific uniquely digitally signed printer driver. The printer is upgraded with a hardware security module (HSM), which can identify the device unmistakably because it holds its own cryptographic module and private key. Print jobs for defined orders are packaged by the brand owner using Public Key Infrastructure (PKI) asymmetric encryption, whereby the STL file goes along with proprietary instructions for the driver regarding the unique objects and their ID. The package is encrypted for the specific printer driver (using its public key) and the printer’s HSM/firmware. Hence, other printer drivers (other workstations) and other printers would not be able to open (decrypt) the package. In situations where no HSM is used, the UUID (universally unique ID) or S/N (serial number) of the printer can be set as a cryptographic salt into the cypher equation, and the printer driver can inquire and verify that S/N whenever the printer is connected. When a print job is an input into the workstation (using the individually signed instruction package), the workstation’s printer driver must “call home” — meaning, connect to the API (Application Programming Interface) listener at the brand’s cloud service, and will verify whether that particular object ID is permitted to print. Before, during, and after a print job, the workstation connects and updates the status, which gets stored in the tamperproof blockchain-powered object-accounting database. Every object has its own record with updates regarding its life cycle indisputably stored. The worker at the remote location cannot conduct prints (production) of licensable objects without the printer driver software connecting to the brand’s API listener, asking for print permission, then decrypting and leaving a trace in the blockchain database. The exact working model of the connection and the possibly multi-layer encapsulated encryption is to be further experimented with. I can imagine a nonce to be issued to the printer driver by the Cloud service solution, and only then can the STL file be decrypted for further processing. Such nonce could be issued conditionally, only if there’s an allowance to print.
Variant B) Use of a dedicated, controlled, remote mini print server In this version, we channel the printing process through a dedicated print server mini-computer, which the brand has control over. It might even belong to the brand. This computer is configured to be used with a specified printer only. The configuration or changes of it can be done remotely via SSH (Secure Shell, a cryptographic network protocol for operating network services securely over an unsecured network) or even a remote-accessible GUI (Graphical User Interface). You can imagine a Raspberry Pi or a similar mini-computer to handle the authorized printing. A secure enclosure is used, perhaps a Zymbit. The mini-computer has to be internet-connected as it will connect to the cloud solution and its blockchain API listener. The above-described mini-computer fulfills various functions, one of them is verifying the serial no. of the printer connected to it. Another one is to receive the (for its own specific key) encrypted print job package via the internet line. And of course, various cryptographic functions, one of them the decryption and verification of the print job to be authorized for exactly the detected printer. And importantly, the mini-computer will connect to the cloud service to notify on events like “print job authorized, printing started, printing in progress, print job completed, etc.”. In case there is no connection to the cloud service, the mini-computer would not be able to function, resulting in no print. The workstation, where print jobs can be “requested” or inserted, would submit them for verification and processing to the cloud platform, which then handles the necessary authentication logic and communicates with the mini-computer to initiate a print job. In the variant B, the workstation is not connected to the printer. If one connected it directly, the printing of our licensable items could not proceed, because the print job needs to be cryptographically processed by both the cloud platform and the mini-computer. All events pertaining to the life of an individual object are saved in the append-only secure database system, the blockchain.
Blockchains like the ones LuxTag is using (especially NEM and SYMBOL) have particularly useful feature sets to account for genuinely unique blockchain accounts with a full set of information that can be stored in them. They incorporate an API-driven architecture that allows them to connect to other parts of web-applications easily. Noteworthy, it is part of blockchains’ nature that only authorized parties can interact with the accounts, and every update transaction is well logged in that account itself. As such, the integrity of the data is pertained with records on the who and when did what to which object. As the first 3D printed liver transplant is expected to happen within only four years to come, let’s give additive manufacturing and its potential the attention it deserves.
Do you have feedback or ideas on security models for additive manufacturing, using technologies like Blockchain, IoT, and other innovative technology? Let me know. We at LuxTag are eager to research, explore, and develop solutions that will power the Fourth Industrial Revolution.
Further reading: Copyright and Related Issues: Copyright and 3D Printing (University of the Witwatersrand, South Africa) 02/Apr/2020
About LuxTag:
LuxTag is an Anti-Counterfeit, Business Insights, and Customer Engagement solution provider, utilizing the blockchain platforms NEM and SYMBOL (previously known as NEM CATAPULT). Luxtag uses a combination of public, private, and hybrid chain services to run its blockchain operations. The service evolves around digitized certificates of authenticity for tangible products, linking these to brands and owners through multi-signature smart contracts and IoT (Internet of Things) elements. Additionally, LuxTag technology provides business intelligence through innovative means of enhanced customer engagement.
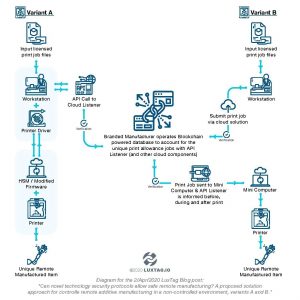 A proposed solution approach for controlled remote additive manufacturing in a non-controlled environment.
A proposed solution approach for controlled remote additive manufacturing in a non-controlled environment.
Rene Bernard
LuxTag Sdn.Bhd. (Malaysia), Director & Co-Founder



